Authenticated OpenVAS Scanning
Authenticated scanning allows the HostedScan agent to log into systems during vulnerability scans, providing deeper visibility into potential security issues that are only detectable when the scanner has authenticated access to the target systems.
Authenticated scanning provides more comprehensive results by allowing the vulnerability scanner to access internal system information, configuration files, the registry, and installed software that would otherwise be hidden from external scans.
Our Free and Basic plans allow setting up and running the internal network scanner to do a Host Discovery scan. This will not impact your plan usage. To perform a full authenticated vulnerability scan, a Premium or MSP plan is required.
What is Authenticated Scanning?
When performing internal network vulnerability scans, the scanner typically only sees what's accessible from the network level - open ports, running services, and externally visible configuration. However, many vulnerabilities can only be detected when the scanner has authenticated access to the target system.
Authenticated scanning enables the scanner to:
- Check for insecure settings in configuration files
- Identify outdated software versions and missing security patches
- Detect weak passwords, excessive privileges, and account misconfigurations
- Verify compliance with security baselines and best practices
- Find issues that are only visible from inside the system
Supported Credential Types
The HostedScan agent supports two types of credentials for authenticated scanning:
-
SSH Credentials: Used for authenticating to Linux/Unix systems via SSH.
-
SMB Credentials: Used for authenticating to Windows systems via SMB/CIFS. Can also authentic to *nix systems with SMB enabled.
Managing Credentials
Credentials are managed directly on the scanning server using the HostedScan agent command-line interface. The agent provides several commands for credential management:
All credential management commands must be run on the scanning server where the HostedScan agent is installed.
Listing Credentials
To see all configured credentials:
./hostedscan-agent --list-credentials
This displays all available credentials with their names and types.
Creating Credentials
To create a new credential for authenticated scanning:
./hostedscan-agent --create-credential
The command will guide you through the process:
- Select credential type: Choose between SSH (Linux/Unix) or SMB (Windows)
- Enter username: Provide the username for authentication
- Enter password: Enter the password (input will be hidden)
- Confirm password: Re-enter the password to confirm
- Name the credential: Give the credential a descriptive name
Example session:
Create a credential for authenticated scanning. This will allow the scanner to log in to machines and inspect internal information. Credentials types include:
1. SSH username/password
2. SMB (Windows) username/password
What credential do you want to create? 1 for SSH or 2 for SMB (Windows): 1
Enter username: scanuser
Enter password: ********
Confirm password: ********
Enter a name for this credential: Linux Admin Account
✅ Credential "Linux Admin Account" created.
SMB credential formats supported:
DOMAIN\usernameusername@domain
Testing Credentials
Before using credentials in a scan, you can test them against a specific target:
./hostedscan-agent --test-credential
The test process:
- Select a credential from your available credentials
- Enter target IP address to test against
- Specify port (for SSH credentials, default is 22)
- The agent runs a quick scan to verify the credential works
Example session:
Select a credential to test:
1. Linux Admin Account [SSH]
2. Windows Domain Account [SMB]
Enter credential number to test (1-2): 1
Enter the IP address to test: 192.168.1.100
Enter the port to test (default: 22): 22
Test started. It may take a few minutes to complete.
Waiting for test to complete. Progress: 25%
Waiting for test to complete. Progress: 50%
Waiting for test to complete. Progress: 100%
Test completed
✅ Successful login!
Updating Credentials
To modify an existing credential:
./hostedscan-agent --update-credential
You can update the username, password, or both. Press Enter to keep the current value unchanged.
Deleting Credentials
To remove a credential:
./hostedscan-agent --delete-credential
You cannot delete a credential that is currently in use by scan targets. Wait for the scan to finish or stop it if necessary.
Running Authenticated Scans
Once credentials are configured on the agent, they become available in the HostedScan web interface for use in scan configurations.
Using Credentials in Scans
- Navigate to the Targets page in your HostedScan dashboard
- Click the "Scan" button next to your internal network source
- Enter the target IP range (CIDR notation)
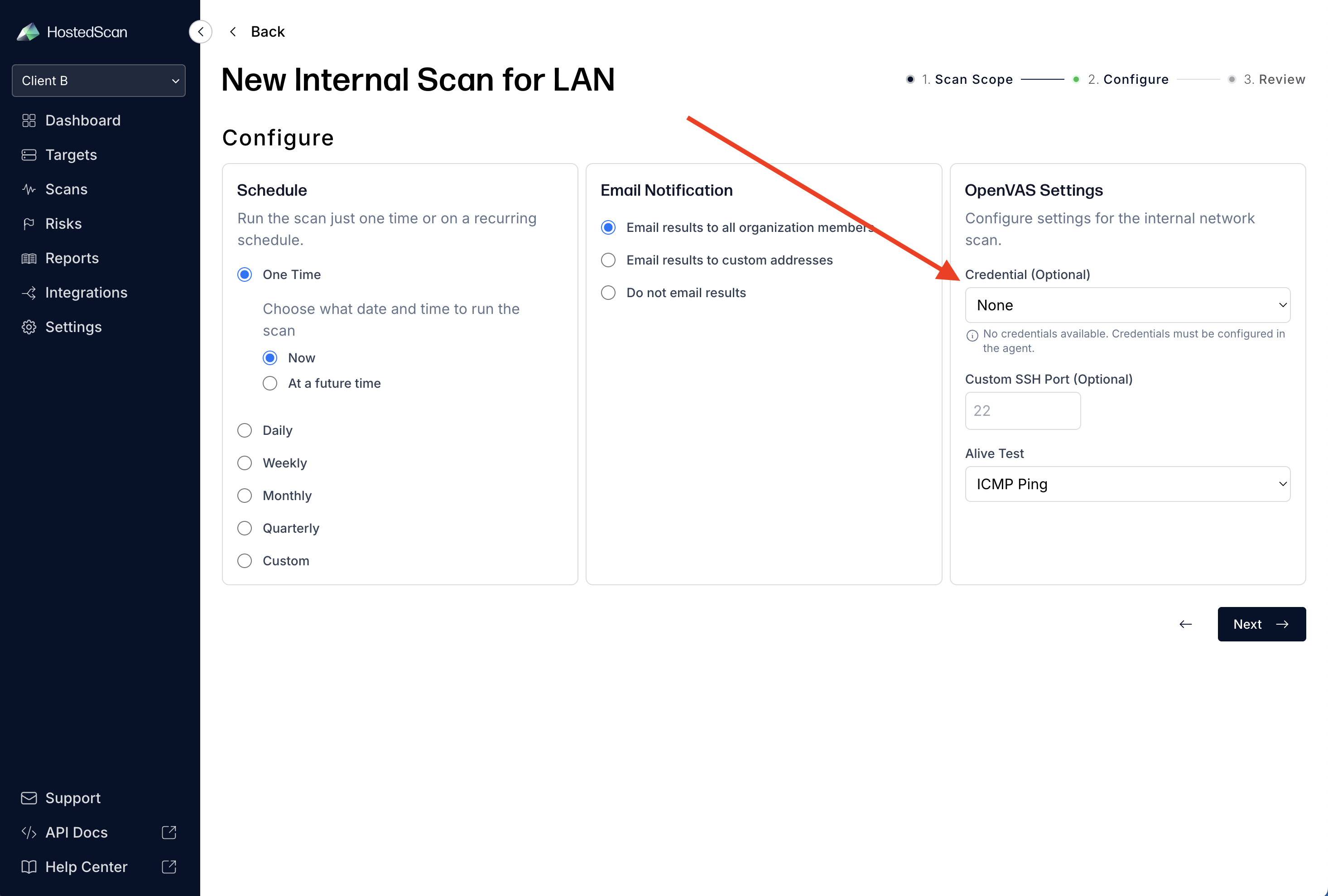
- Configure OpenVAS Settings (this section appears when scanning internal networks):
- Credential: Select from available credentials configured on the agent
- Custom SSH Port: If your systems use a non-standard SSH port (default: 22)
- Alive Test: Choose how the scanner determines if systems are online
For an explanation of the OpenVAS settings, see OpenVAS Settings Explained
The OpenVAS Settings section will only appear when configuring scans for internal network sources that have the HostedScan agent installed.
- Confirm the settings and click the "Run Scan" button
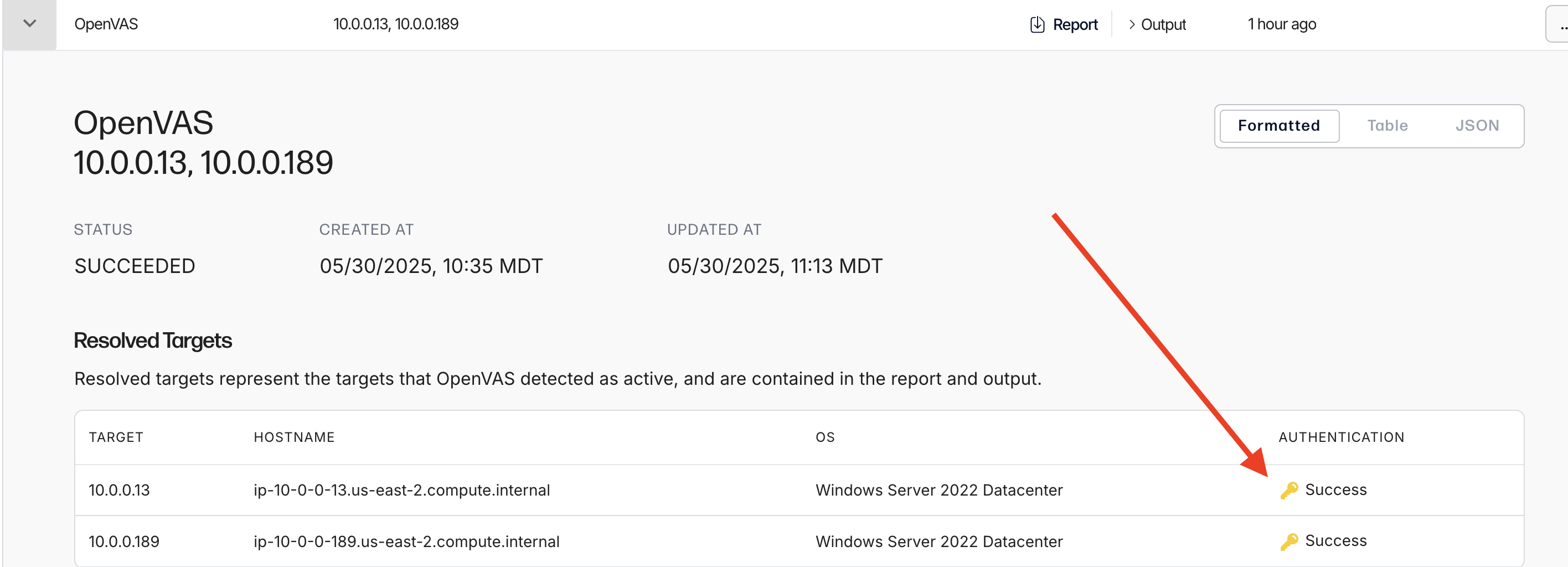
Once the scan has run, you can verify the login status of each machine by clicking on the scan in the scans table. The expansion shows each detected target, along whether or not authentication succeeded for that target.
OpenVAS Settings Explained
Credential (Optional)
- Select a credential for authenticated scanning
- If no credential is selected, the scan will run unauthenticated
- Credentials must be configured on the agent before they appear in this list
Custom SSH Port (Optional)
- Specify if your SSH services run on a non-standard port
- Leave blank to use the default port (22)
- Only applies when using SSH credentials
Alive Test
- ICMP Ping: Uses ping to check if systems are online (fastest)
- ICMP & TCP-ACK Service Ping: Combines ping with TCP checks (more thorough)
- Consider Alive: Assumes all IPs in range are online (slowest but most comprehensive)
Troubleshooting
Credential Test Fails
- Verify the username and password are correct
- Check that the target system is accessible on the network
- Ensure the appropriate service (SSH/SMB) is running on the target
- Verify firewall rules allow connections from the scanning server
Credentials Don't Appear in Web Interface
- Ensure credentials are created on the same agent/source
- Check that the agent is connected and running
- Verify the agent has successfully synchronized with HostedScan
Limited Scan Results with Credentials
- Check that the scan account has sufficient permissions
- Verify the account can access system directories and files
- Review scan logs for authentication errors or permission issues
Need Help?
If you encounter issues with authenticated scanning:
- Test credentials using the
--test-credentialcommand to isolate authentication issues - Check agent logs for detailed error messages:
journalctl -u hostedscan-agent.service -f - Review scan results for authentication status and any error messages
- Contact support at hello@hostedscan.com for assistance