Introduction
Welcome! HostedScan is a comprehensive vulnerability scanning and management platform. Scan your websites, servers, networks, and APIs. View dashboards, get threat alerts, and generate audit-ready reports.
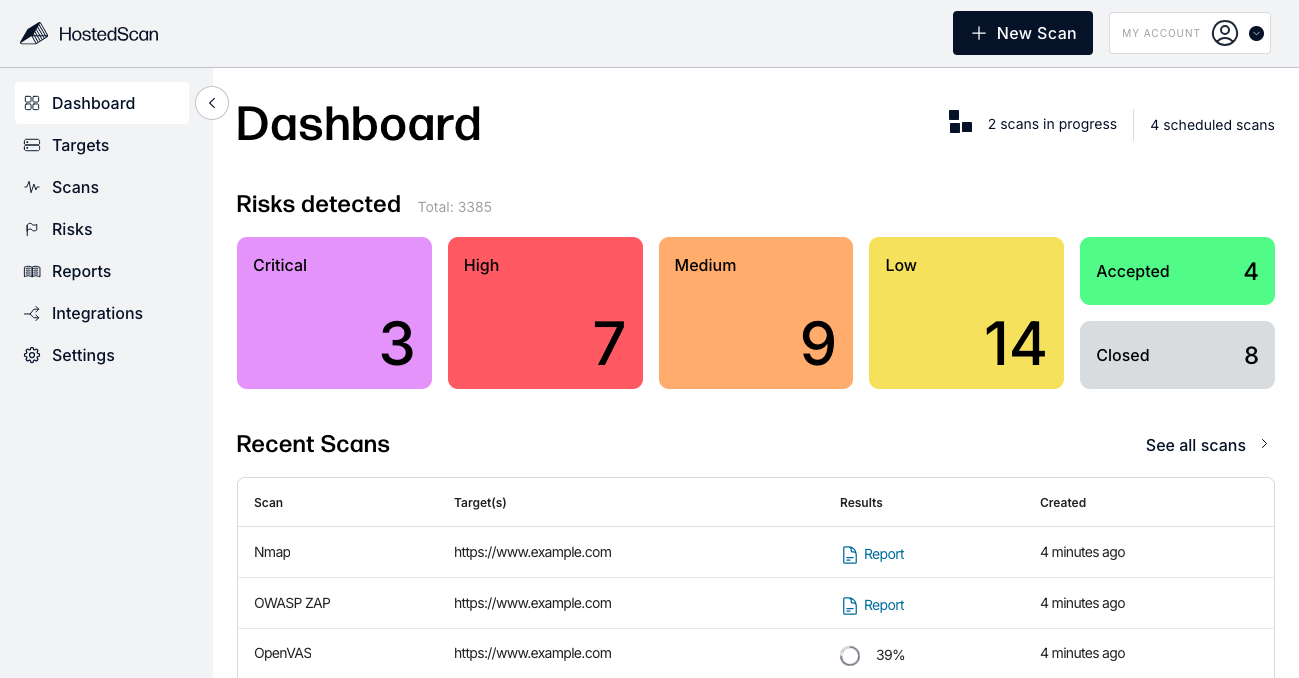
Getting Started
The best way to get acquainted with HostedScan is to create an account and start running some scans. Try it out here!
Then refer to this documentation for details on how to use specific features.